Hacked Website Protection and Recovery Frequently Asked Questions
This FAQ provides hopes to provide non technical website and business owners FAQ to some security related question and practices.
If have any more questions that is not in the FAQ, feel free contact me via twitter
More Questions“Prevention is better than cure”

I found this image on Reddit with the caption - admin:admin It's technical joke
Criminals use password dictionaries and share compromised sites on the darknet. Password dictionaries include the most commonly used passwords. Password dictionaries help bots (robotic software) repeatedly attack a system or website. If a password is weak, chances are a system can be broken into quite quickly. At iautomate.cloud, we often see server logs fill up with this type of attack. It’s referred to as a brute force attack and low in sophistication. It’s like trying out different house keys until one fits. They are a very tenacious crowd and only have to get through once while you have to protect 100% of the time. I can lead a team to uncover the faults in your solutions.
A big question, which has far to much information for this FAQ. Careers are built around the answer. There are teams of experienced people who can solve such problems. I can help with selection and team buidling to have indviduals and teams interested and engaed in their work. The most basic advice:
The most basic recommendation, review your password behaviour. A lack of a secure password is an all to common method of breaching software.
Not all security breaches are password related. I personal, have common software used by some hosting providers and moved a site over to AWS. Contact me to find the right people for a review of your environment, I can lead the team.
Strong password means one that uses uppercase and lowercase letters, numbers and symbols all mixed up. Keep passwords random. The size should be between 8 to 12 characters or greater. Don’t use passwords that mean anything. The more random, the better. Some suggest multiple words in a sentence can also work.
Yip, nor can I. This should not be an excuse to justify a weak password. Criminals have improved brute force attacks with commonly used passwords. See the password dictionaries section earlier.
To get over this matrix glitch which your memory has introduced, use a password manager. It’s so much easier as it stores and randomises your selection of passwords so you don’t have recall them. We all have better things to do.
Additionally, don’t reuse passwords. You might find it tempting to reuse passwords on different systems and sites. Don’t! Criminals find this a handy way piggybacking there way from one system to another.
You probably should use one. Saves on working memory. There are a few around.
Apple Mac has one built into the operating system called KeyChain. It can be setup to work on many devices at the same time, including your iPhone.
Google Chrome has a built in password manager which works on many devices at the same time. You’ll need to configure Chrome for this to work and have a Google account. Suggestion, use MFA with it. (What’s MFA?)
KeyPass and KeePassX are popular options and available in many flavours for your prefered operating system, windows, mac or linux.
As an iautomate.cloud customer, well already have recommended using a password manager and MFA.
Passwords are difficult to remember. A password manager simplifies the management of strong passwords and secures them in an encrypted database.
Once you have adapted to the new behaviour, the pain of change is forgotten and you save yourself time trying to remember passwords. Keep in mind, that your password managers become your next weakest link. Rotate your passwords regularly.
Multi Factor Authentication, also known as two-factor authentication. Many systems offer this as a service. MFA is like having a password that expires. Some systems authenticate via other means. For instance a mobile text message sent to your phone, requiring you to enter text on a site.
Google Authenticator is a good solution that many sites work with. With MFA the risk of a bad password is less onerous. If you do forget to rotate your password, at least you have the MFA challenging access. Google Authenticator acts like a constantly changing password.
Default usernames and passwords are common knowledge and used on many systems for initial setup. It’s best practice is to disable default usernames and passwords. Criminals use lists of default passwords and usernames to brute force systems. Read about dictionary brute force attacks. For instance, the default username for WordPress is admin and the login screen can be found at yoursite.url/wp-admin
Many hacks begin by sending an unsuspecting email in the hope that a viewer will click on an email bait, also known as a phishing attack. The fraud attempt is disguising as a trustworthy entity. An email may contain a computer virus, malware or ransomware.
Our recommendation is to migrate your email system over to a Cloud provider that has a robust spam filtering systems. You could try Google For Business Microsoft Office 365 for Business (Contact me for implementation and references). Here’s Microsoft's commitment to security.
There are a plethora of options. Do your research or contact us for recommendations.
This is a broad topic. The answer depends on your personal and business circumstances. We suggest you get in touch for a review and recommendations.
Prevention is better than cure, of course. However, there are many systems that can help you protect and monitor your software and alert you about security events.
AWS has Amazon GuardDuty and a host of other systems to help protect your assets on the AWS Cloud.
Google Cloud has Cloud Security Scanner.
There is also the likes of TripWire for server installations in an organisation.
Unfortunately, some small and medium sized organisations often fail to find out until their customers tell them.
The most basic method is after the fact when your site is added to the Google Chrome malicious list. The warning appears in red with the text “Deceptive Site Ahead”. You can try confirm this by browsing the site from a VPN in a Chrome Incognito Session.
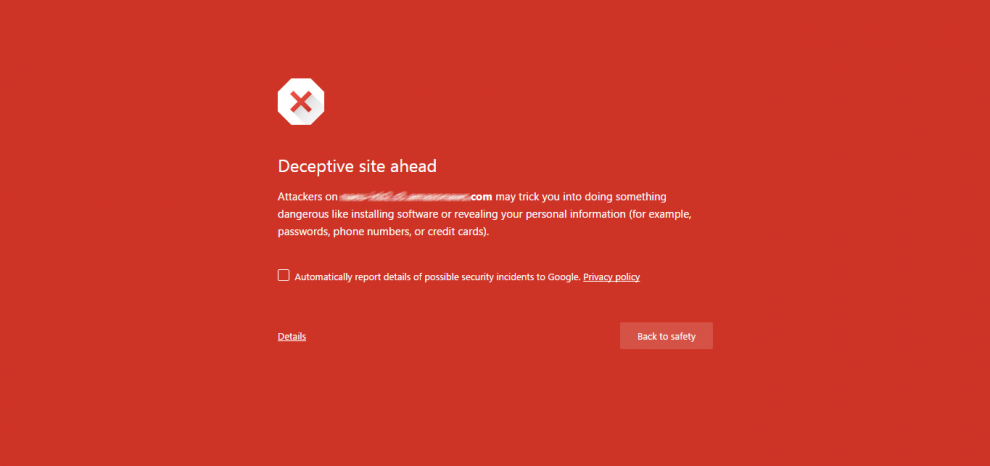
The next step is to study the anomalies. These are signs you should not ignore. For instance, your site analytics might indicate you have an unusual spike in traffic, which is inconsistently high and cannot be explained. Sometimes log files fill with unusual behaviour. Although, you might only be paranoid and chasing ghosts.
Confirmation often requires additional software and a thorough analysis of your environment. File permission changes, log file data, access times, emails going to a customers SPAM…. these signals go on.
Computer forensics can become complex and best left with the experts. If you require forensics, please contact us so we can provide the appropriate service level.
Yes, there is always the “Get me out of here” option. With this service, we’ll lift, shift and harden your environment. Harden means we apply security best practice to your system.
We work with any hosting provider of your choice. However, we are accredited to working with Amazon Web Services (AWS) and have experience with Google FireBase. For email see our previous recommendations.
Don’t panic! If your website or domain has been hacked we are here to help recover your business reputation and website. You’re organisation is recoverable. You need to inform us whether you intend taking lawful action against the intended hackers or you want the “Get me out of here” option.
Many countries mandate disclosure of a data breach to government authorities. It’s important that you know your countries specific data breach disclosure laws.
This is when a website is targeted by criminals to reduce the Google ranking. Organisations or individuals purposefully try to negatively impact a websites search ranking. It is not acceptable practice.
A hacked site could cause your Google ranking to plummet if labeled as malicious. In certain circumstances Google may delist your site from their search engine. For instance, if the site is malicious or if the site has engaged in unacceptable ranking practices.